

Why did this guy turn against Morales?


Why did this guy turn against Morales?


Say what.


I think so. A relatively small subset of the video upload firehose at YouTube who produce rewatchable content is going to require a lot less resources to provide than doing a free-for-all upload-anything video. This might actually be feasible.


It absolutely is on an individual level in a system where capital decides who writes the laws and who gets justice. The way you push back is by organizing as a class or at least a group.


There’s one in the article comments. Talks about getting the material “dishonestly” and violating the TOS.


WTF is Premium Lite?


Uhhh wtf is happening?
Nothing, it’s the standard protocol. They’re currently dealing with the results of a previous activation.


For a while at least.


Is this the militia that was reported operating in IDF-controlled aid zones?
You can do encrypted swap as well. If you use the same passphrase you can install decrypt_keyctl and use it as described here. It will cache the passphrase and send it to every other LUKS volume that needs decrypting so you have to type it only once. This is what I’m currently using and my root is on ZFS on LUKS.
Another option which I haven’t used is to have a small volume that only stores your LUKS keys as files, then your LUKS volumes reference those files as keys, then you decrypt only that volume with a passphrase upon boot.
Another option is to use a swap file. I used to run Ubuntu LTS on LUKS on LVM. That is disk > EFI and LVM partitions > LVM volume boot, LVM volume for LUKS > root filesystem inside LUKS > swapfile in that root filesystem. Upon boot, GRUB is able to read the Linux kernel straight from the boot volume on LVM. Boots the kernel. You get a prompt to decrypt the LUKS volume where the root filesystem is. Once decrypted, the kernel can access the swapfile if it needs to resume from it. If I didn’t use ZFS, I’d be using this scheme as it’s superbly flexible. Growing the volumes and filesystems for larger storage is easy. Adding redundancy via LVMRAID is easy. Changing the swap size is easy. Hibernation works.


Does anyone know if there’s additional sandboxing of local ports happening for apps running in Private Space?
E: Checked myself. Can access servers in Private Space from non-Private Space browsers and vice versa. So Facebook installed in Private Space is no bueno. Even if the time to transfer data is limited since Private Space is running for short periods of time, it’s likely enough to pass a token while browsing some sites.


This aren’t looking good internally either.
Talking to my structural engineer friend about the way we build software makes him sad every time. And I’m not even talking about vibe coding. Yet.
Yup. It’s completely inconsistent in its interpretation of the + operator.


Still trying to pass Bluesky as federated I see.
This is too stupid so I had to check.
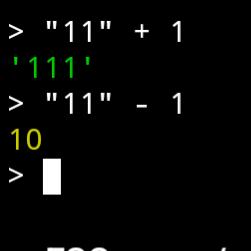
Fuck me.
Do they have a repo?
It’s more than a packaging format but yes. It includes all dependencies needed to run the main program in a container but the kernel. It’s a complete separate root filesystem. When you run it, as intended, a single process is started which loads all the things it needs from that filesystem. It’s isolated from the rest of the system unless you share resources with it, like directories or special devices. Obviously this results in larger packages but there is a clever way to save on that overhead with layering, so in practice while still significantly larger than single program deb files, it’s not nearly as bad as it sounds. The thing is that Flatpak and Snap also package dependencies to a different degree.


Countdown till Trump complains about Canada over this.
Oh yes, please create a new party buddy.